Siesta Time: User Guide¶
Siesta Time is a red team framework with the purpose of automating and facilitating implants creation and their C2 Infrastructure.All these actions keeping trace of what your Operators are doing.
- Save your Different Network Infrastructure Elements
- Save units of virtual private cloud,domains and software as a service credentials to be able to deploy C2 infrastructure.
- Deploy Implants that adapt to your current target
- Select Implant configuration,modules and set of redirectors. The different modules available will define how the implant will egress, persist in target foothold… The output will be binaries for different devices and the working C2.
- Maintain Access and Interact with your foothold
- Once the delivery process is successful and the implant is executed, list your infected devices. Interact with them to send essentials commands or put them to sleep.
- Deploy Post. Exploitation Servers for Lateral Movement
- With the objective to achieve further target’s assets from their intranet, Siesta Time can use your resource battery to deploy “shorted lived” handlers (ssh,msf,empire…)
- Document the whole Operation to provide insights to the target institution’s Blue Team or Stakeholders
- Reporting will focus on saving every framework job and action execute in footholds or Post. Exploitation handlers.
Installation¶
SiestaTime installation needs just two elements to work properly, the Hive, normally installed by the operations admin/manager, and the client, for the Operators.
Note
Installation for both Hive and client is designed for the moment just for Ubuntu (tested on Ubuntu 18.04.4 LTS)
Everything related to the installation process for both Hive and client will be saved on:
./SiestaTime/installConfig
Adding Resources¶
Saving online infrastructure resources will be the first steps to use Siesta Time. If you don’t desire to use automatic deployment of implants you can always deploy an Offline version of them where just executables will be generated.
Hive Status¶
The Hive Status provide red teamers a bunch of tabs where they can check every job processed by Hive. If any problem appears during the process of these, the Logs will show errors details.
Deployment¶
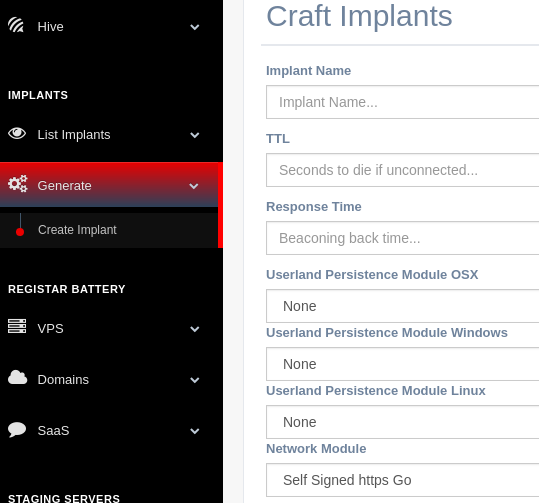
Once the red team has registered every resource that they want to use for their C2 infrastructure these can be use to generate it. Implants (redirectors and executables) and Post. Exploitation servers (droplets,handlers…)
- Implants: Basic Config. | Network Modules | Persistence Modules | Redirectors
- Post. Servers: Droplets | Handlers
Interactions¶
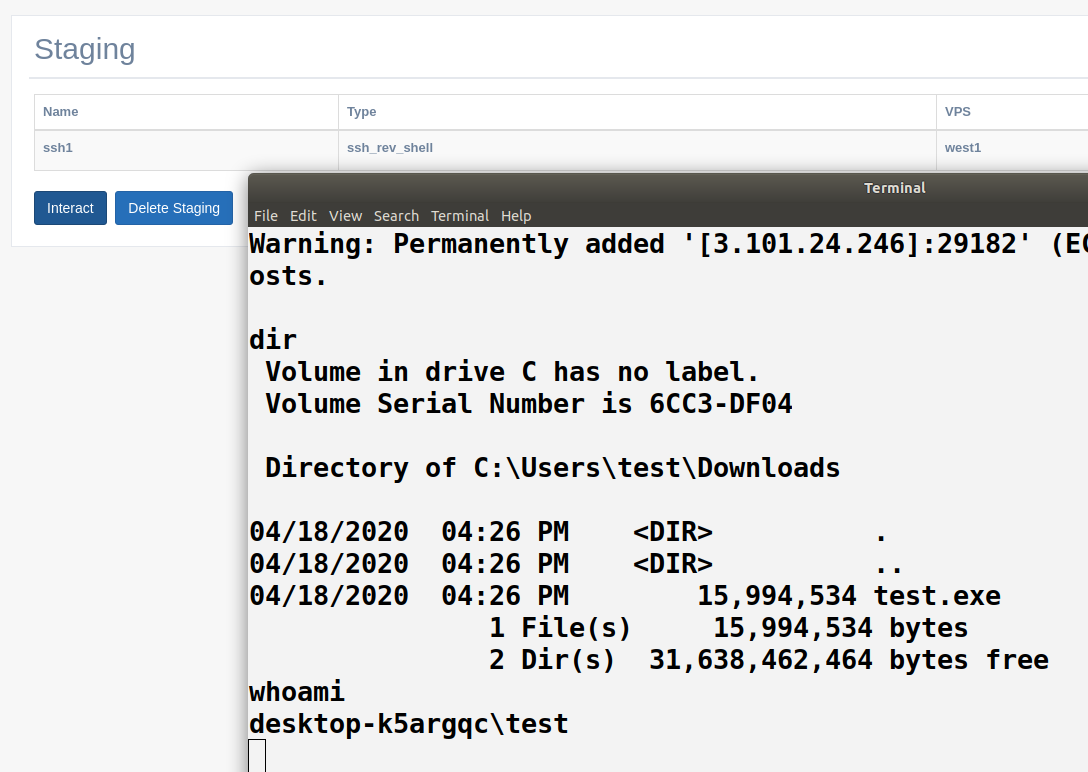
After the deployment the red team should design a kill-chain/attack that requires normally the delivery of the previous generated executable. Once the delivery is successful, Hive will start to receive connections from the foothold. Lateral movement may be required to acquire further target assets. Bichito has the capability to retrieve basic commands that will be used to persists or escalate privileges. If the operator needs a more complex connection to the foothold (ssh,remote desktop, tunnelization…) Post. Exploitation servers will be used. through new processes triggered from Bichito.
Reporting¶
Reports are a way to extract every action performed by Operators using the SiestaTIme framework.